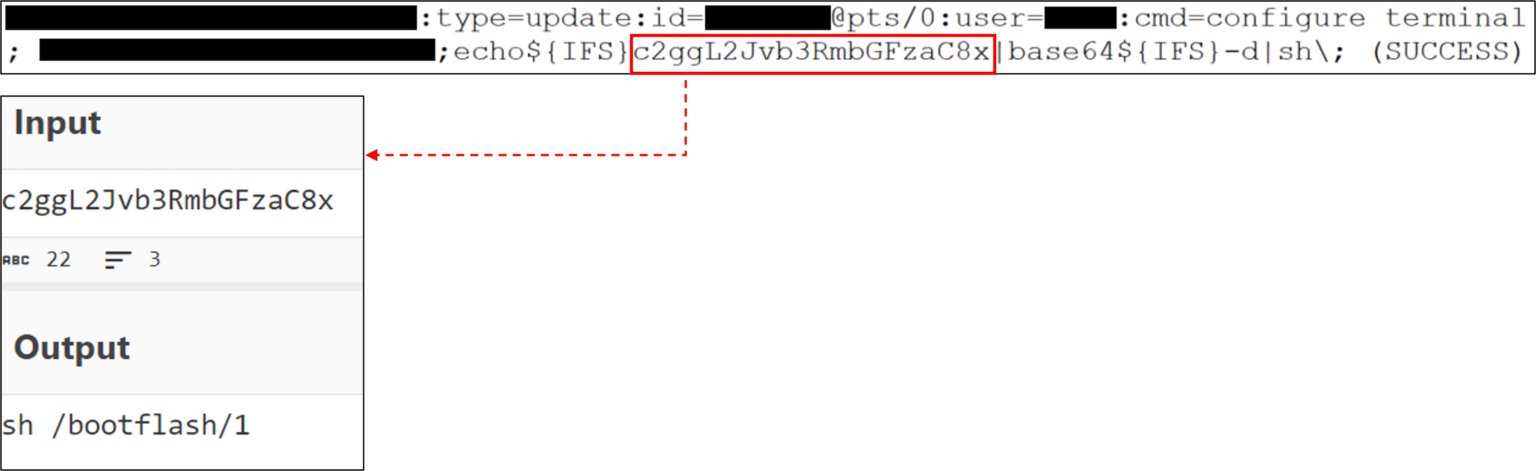
Hi, my fellow malware enthusiast,
I don’t know about you but school just started for me and to be honest, I’m now realizing that I really need a break from everything, except malwares. Don’t worry you will still receive my weekly newsletter. I like to do research, but with school I will have to reduce it, well I’m still good until my midterms, that is when is going to hurt. But, anyway, enough of me venting about going back to school. Enjoy this week newsletter, you will probably spot that I changed the theme color, let me know what you think!
📰In today’s newsletter
Android Malware Targets ATM Information at Three European Banks
Velvet Ant APT Exploits Cisco Switch Zero-Day in Stealth Attack
DDoS Attack Tool Unleashed for Public Use
TA453 Targets Religious Figures with Fake Podcast Invitations
Hiding Data Theft Behind a Fake Windows Update
American Radio Relay League Pays the Price
CISA Highlights Critical Vulnerabilities in Dahua Cameras, Linux Kernels, and Exchange Servers
Microsoft Rushes Fix for Zero-Day RCE Vulnerabilities in Edge
Android Malware Targets ATM Information at Three European Banks

ESET researchers have uncovered a new Android malware strain, NGate, used by cybercriminals to steal ATM information from customers of three Czech banks. Disguised as fake banking apps, NGate leverages NFC technology to capture payment card data from infected devices. Victims are tricked into installing the malicious app through phishing messages and are then prompted to use NFC to transfer card data to the attackers. The stolen information is used for ATM transactions or to transfer funds. Discovered in November 2023, this unique malware technique highlights a serious threat. Users should be vigilant online, verify URLs, secure PINs, disable NFC when not in use, and consider virtual cards for online transactions.
🔗Link
Velvet Ant APT Exploits Cisco Switch Zero-Day in Stealth Attack

Velvet Ant, a Chinese APT group, recently exploited a zero-day vulnerability in Cisco’s IOS XE software, targeting key infrastructure worldwide. This attack allowed the group to gain control over network devices, bypassing security controls to execute malicious commands. The breach was stealthy and difficult to detect, emphasizing the sophistication of state-sponsored cyber operations.
💡We got to hand it out to China, they be finding all the zero-day
Cisco swiftly issued patches, but the incident underscores the critical importance of timely updates and vigilance against advanced persistent threats. Organizations relying on Cisco devices should prioritize applying these patches to safeguard against potential exploits.
🔗Link
DDoS Attack Tool Unleashed for Public Use

The newly released MegaMedusa tool by RipperSec is a powerful, publically available DDoS weapon, capable of overwhelming websites with massive traffic. This tool, which has gained popularity among threat actors, can generate over 10 million requests per second, making it one of the most dangerous DDoS tools available. Its ease of use and effectiveness pose a significant threat to online services, especially those lacking robust defenses.
💡Honestly speaking DDoS has to be one of the most simple but devastating attacks! I’m sure you would agree too!
Organizations are urged to bolster their DDoS mitigation strategies to protect against potential MegaMedusa attacks, which can cripple websites and disrupt business operations.
🔗Link
TA453 Targets Religious Figures with Fake Podcast Invitations
The Iranian cyber-espionage group TA453, also known as Charming Kitten, has launched a new spear-phishing campaign aimed at high-profile religious figures. Posing as podcast producers, the attackers send fraudulent invitations to lure targets into downloading malware-laden files. The malicious documents are disguised as interview details but instead install malware designed to steal sensitive information. This campaign reflects TA453’s sophisticated social engineering tactics, which exploit trust to gain unauthorized access to critical data.
💡Charming Kitten?? In a sense they are charming people into downloading their malware, so i guess the name makes sense😂
🔗Link
Hiding Data Theft Behind a Fake Windows Update

The "Mad Liberator" gang has raised the stakes in cyber deception with a new tactic: disguising data theft behind a phony Windows update screen. By masking their malicious activities as routine system updates, this group skillfully evades detection and misleads victims into believing their systems are undergoing normal maintenance. This innovative approach not only facilitates stealthier data exfiltration but also highlights the ever-evolving nature of cybercriminal tactics.
💡You should know it about now; there will never be a newsletter without windows in it. Forget it!
🔗Link
American Radio Relay League Pays the Price

The American Radio Relay League (ARRL) has confirmed a staggering $1 million ransom payment, highlighting the escalating costs of ransomware attacks. Targeted by cybercriminals, the ARRL chose to pay the ransom to recover their compromised systems and data. This bold move underscores the severe impact ransomware can have on organizations, revealing the tough choices they face under cyber duress. As ransomware demands reach new heights, it's a stark reminder of the critical importance of proactive cybersecurity measures and preparedness to protect against such high-stakes threats.
🔗Link
CISA Highlights Critical Vulnerabilities in Dahua Cameras, Linux Kernels, and Exchange Servers

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent update to its Known Exploited Vulnerabilities catalog, spotlighting severe flaws in Dahua IP cameras, Linux kernels, and Microsoft Exchange servers. These vulnerabilities are currently being exploited in the wild, making them a pressing concern for all affected systems. This alert underscores the crucial need for immediate patching and robust security measures to defend against active attacks.
🔗Link
Microsoft Rushes Fix for Zero-Day RCE Vulnerabilities in Edge

Microsoft has released an urgent update for its Edge browser, addressing a critical zero-day vulnerability (CVE-2024-7971) currently being exploited. This flaw, found in Chrome's V8 JavaScript engine, allows remote code execution through a malicious HTML page. The update, Edge Stable Channel Version 128.0.2739.42, resolves 25 vulnerabilities, including five specific to Edge. With CVE-2024-7971 actively targeted by attackers, users are strongly advised to update immediately to prevent potential data breaches, malware, or system takeovers.
💡Who still uses Edge as a browser…?👀🙋♂️
🔗Link
Cybercriminals Exploit Popular Software Searches

Cybersecurity researchers have identified a troubling rise in malware infections originating from malvertising campaigns distributing a loader called FakeBat. This malware, also known as EugenLoader and PaykLoader, targets users searching for popular software like Brave, Zoom, and KeePass by redirecting them to fake websites that host trojanized installers. Once downloaded, FakeBat executes malicious scripts that install secondary payloads, including notorious malware like IcedID and Carbanak. The attackers, linked to a group known as UNC4536, are using this method to deliver Malware-as-a-Service (MaaS) operations, posing a significant threat to anyone downloading software from unverified sources.
The sophisticated attack leverages drive-by downloads and exploits users' trust in well-known software, making it difficult to detect. FakeBat not only gathers critical system information but also ensures persistence by creating shortcuts in the system’s StartUp folder. This campaign highlights the importance of downloading software from official sites and remaining vigilant to avoid falling victim to such deceptive tactics.
✉️ Wrapping Up
In the world of malware, understanding is key. As we delve into these threats together, remember that knowledge and vigilance are our best allies.
If you find this newsletter helpful and know others who might benefit from it, I'd be grateful if you could pass it along. 🙏
Until next time, stay informed and keep your defenses sharp. Here’s to staying one step ahead
Thanks for reading!